In the ever connected era, cloud computing is altering the way medics, nurses, and hospitals deliver quality, cost-effective services to their patients. The Health Insurance Portability and Accountability Act of 1996 (HIPAA) is a law in the US published to protect privacy of patient’s medical records and health related information provided by/to patients, also known as PHI (Personal Health Information). HIPAA applies to “covered entities” and “business associates” including doctors, hospitals, health related providers, clearing houses, and health insurance providers. HIPAA is also
HIPAA Requirements
For HIPAA compliant solution, every Covered Entity and Business Associate who accesses the PHI, must ensure technical, physical and administrative safeguards are in place and addressed, which ensures the HIPAA Privacy Rule to protect the integrity of PHI. If any breach of PHI occurs, then solution implements the notification procedure to notify the breach (HIPAA Breach Notification Rule).
Find below HIPAA requirements to be fulfilled while designing HIPAA compliant cloud connected healthcare solution.
HIPAA Security Rule
HIPAA security rules address the standards that must be applied as safeguards to protect data in REST and transit. This applies to all humans and systems that have access to confidential patient data. The system must implement RBAC (Role Based Access Control) which helps to define different levels of access to different entities who are accessing the ePHI like humans (researcher, patient, doctor) or systems (smart devices, mobile, tablets).
Technical SafeGuard:
Technical safeguard focuses on the technology used to protect ePHI and provides access to data. The data in REST and transmit must be encrypted to NIST standards once it travels beyond the organization’s internal infrastructure. This focuses on following parameters.

Physical Safeguard:
Physical safeguard focuses on physical access to ePHI irrespective of location. ePHI could be stored on remote location or on-premise data center of HIPAA covered entity. In any case, the physical location where ePHI is stored must be secured and prevent unauthorized access.
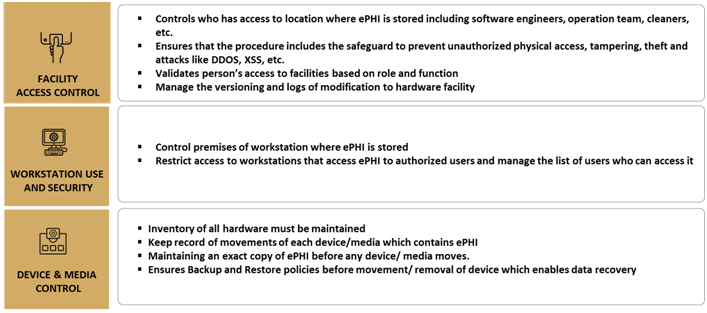
Administrative Safeguards
Administrative safeguard focuses on procedures and policies which bridge privacy rules and security rules together.
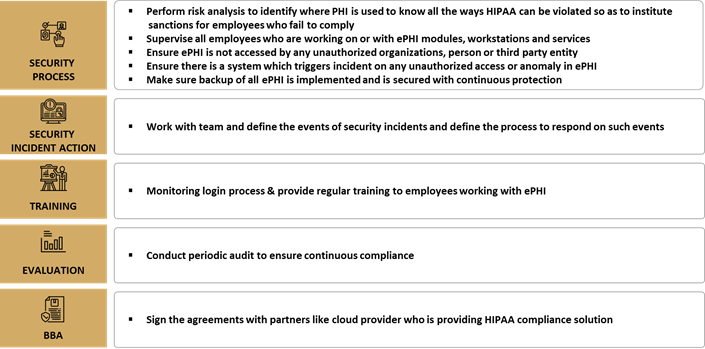
HIPAA Privacy Rule
HIPAA Privacy rules focus on how ePHI should be used and disclosed. The rule demands that all required safeguard is implemented to protect a patient’s personal information. The rule gives authority to patients – right of information, right to obtain a copy of information and share the information.
As per privacy rule, covered entities must respond to patient requests within 30 days.
It is advisable to,
- Provide training to employees
- Ensure appropriate actions are taken to maintain the integrity of ePHI
- Written permission is must from patients, when their health information is used for any purpose like marketing, research etc
HIPAA Breach Notification Rule
HIPAA breach notification rule requires covered entities to notify patients when there is a breach of their ePHI. It should also be further notified to the Department of Health and Human Services(Only if breach affects more than 500 patients).
Notification notice should include:
- Type of ePHI involved
- If known,share unauthorized person’s details who accessed the ePHI
- Is ePHI viewed or acquired?
- Reason of breach and risk mitigation plan
HIPAA Omnibus Rule
HIPAA omnibus rule addresses areas that have been omitted in previous HIPAA updates.
It clears definitions, clarifies procedures and policies that are implemented for HIPAA compliance checklist to cover business associates and subcontractors.
It amends HIPPA regulation on following key areas:
- Final amendments including penalty structure as required under the Health Information Technology for Economic and Clinical Health (HITECH) Act
- Updating the harm threshold and including the rule on breach notification for Unsecured Protected Health Information under the HITECH Act
- Modification of HIPAA to include the provisions made by the Genetic Information Nondiscrimination Act (GINA) to forbid the disclosure of genetic information for underwriting purposes
- Preventing the use of ePHI and personal identifiers for marketing purposes
HIPAA Enforcement Rule
HIPAA Enforcement Rule covers Investigation on breach of ePHI and the penalties on the entities who are responsible for breach of ePHI. As per HIPAA compliance checklist, following are penalties.
- A violation attributable to ignorance can attract a fine of $100 – $50,000
- A violation which occurred despite reasonable vigilance can attract a fine of $1,000 – $50,000
- A violation due to intentional negligence which is corrected within thirty days will attract a fine of between $10,000 and $50,000
- A violation due to intentional negligence which is not corrected within thirty days will attract the maximum fine of $50,000
HIPAA Risk Assessment Guidance
Following are guidelines for risk assessment.
- Identify the PHI which solution creates, receives, transmits and stores
- Identify threats to the integrity of PHI – human threats including those which are both intentional and unintentional
- Identify the measures in place to protect against threats to the integrity of PHI, and the likelihood of a “reasonably anticipated” breach occurrence
- Determine impact of breach and define potential occurrence of a risk level based on the average of the assigned likelihood and impact levels
- The rationale for the measures, procedures and policies subsequently implemented, and all policy documents must be kept for a minimum of six years
Thus, to comply any healthcare solution for HIPAA, following requirementsshould be taken care and integrated in the solution:
- Ensure Safeguards to protect PHI on physical and virtual data storage and transfer
- Limit the usage and access of information with proper access controls
- Have proper Agreements to cover functions and activities. BAA to ensure that service providers use and pass the PHI with proper access and follow the defined safeguard
- Define the training change processes, approval processes for access controls and management processes
- Setup training program for employees on PHI protection awareness, security and process explanation
At VOLANSYS, we help healthcare device manufacturers and solution providers to comply their healthcare devices/solutions for HIPAA following above rules and regulations.Our capabilities include device miniaturization, designing low power customized wearables, invasive and non-invasive devices, security compliances, HIPAA compliant cloud services and much more.

About the Author: Chandani Patel
Chandani is AWS Certified Solution Architect, AWS Business & Technical Professional, Technical Lead on several domains – Cloud Solutions, IoT Solutions, ML&Data Science. She is Cloud Solution Architect with expertise in designing, developing and architecting cloud solutions for public clouds (Azure, AWS, Google & Bluemix), private clouds & hybrid clouds.









