The adoption of Edge computing is on the rise despite the COVID-19 pandemic having spurred fundamental disruption. Edge Computing enables real-time data processing at the edge, reducing the amount of traffic sent to the cloud and processing time for critical applications in healthcare such as remote health monitoring of patients, where real-time data communication is crucial.
While edge computing solves huge data traffic issues in the IoT ecosystem, it is subject to its security vulnerabilities. Edge devices are often a target for intruders, attackers because these edge devices are an entry/exit point for data to flow between the sensors, connected data centers, or cloud networks. Thus, managing the number of edge devices is a security nightmare.
Common Security Challenges of Edge Devices
A typical IoT Edge Device faces attacks from different forefronts: software IP thefts, stored keys theft, fault injection, malicious applications, attacks from peripherals, etc.
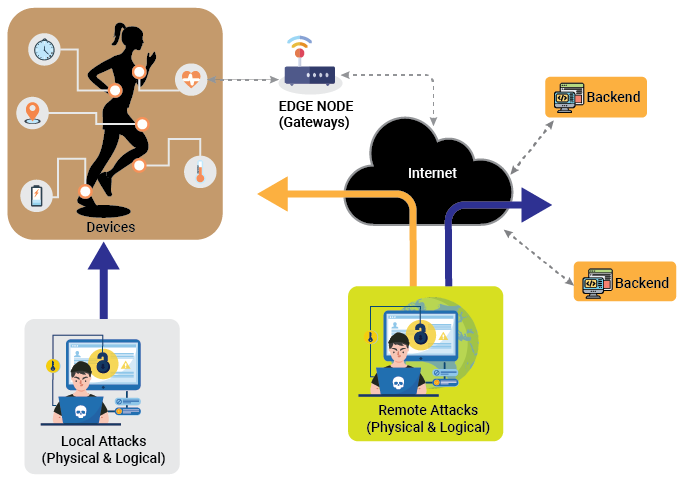
They are performed by accessing both wired and wireless standard interfaces. Edge devices, whether maintained by end-users or enterprise administrators have such security challenges. Some of the common problems that have led to exploitable vulnerabilities are:
- Default configuration settings: Some wireless access points may have outdated or Insecure WEP or WPS wireless security services enabled by default. Such standards could allow attackers in range of the device to gain access to the network
- Outdated firmware: If the firmware is not updated for a prolonged time, either by the manufacturer or the user, it may lack current security features, such as distributed denial-of-service (DDoS) mitigation, which could help thwart common attacks
- Challenges with scaled deployments: Medium and large enterprises experience difficulty in managing these types of devices as they scale up to large network infrastructures
To overcome such challenges, OEMs and enterprises need to understand how to secure IoT Edge Devices. What are the best practices to guard edge workloads and data against possible attacks?
Managing Security Risks at Edge Devices
Although many edge devices include native security capabilities, such as wireless APs or virtual private network (VPN) servers designed to block a malicious user or device connection. Organizations must consider how best to implement these security features and other security methods such as device configuration and management, encryption, cryptography, system visibility, continuous monitoring, and access control to prevent the device from being exploited.
- Patch All Edge Devices
Attackers are continuously finding new flaws in existing devices and their embedded software. Once a vulnerability is found, it is essential to patch it as soon as possible to prevent an attacker from using it to gain unauthorized access to the device.
- Ensure Encryption Between Multiple Edge Devices
Synchronization between devices may include valuable information such as cryptographic keys and credentials, but this communication is often unencrypted by default. Use a truly random mechanism for the source of entropy during cryptographic key creation.
- Security Algorithm For Communication
RSA (Rivest–Shamir–Adleman) algorithm: A user of RSA creates and then publishes a public key based on two large prime numbers. The prime numbers must be kept secret. Anyone can use the public key to encrypt a message, but only someone with knowledge of the private key can decrypt the message.
- PRINCE Real-time Encryption/Decryption
PRINCE algorithm is used for real-time encryption and decryption for on-chip flash. Compared to AES, PRINCE is fast because it can decrypt and encrypt without adding extra latency.
- Implement Multi-factor Authentication(MFA)
MFA can be implemented both for systems designed to control administrative access to edge devices and for VPN connections. Alternative methods for MFA, such as authenticator applications, software tokens, and phone call verification are more secure to protect devices.
- Visibility and Automated Monitoring
Automated monitoring can provide detailed and holistic system visibility in which software is used to scan the network and analyze logs for anomalous behavior. For example, AI algorithms run over those devices and the data generated help in understanding the behavior of the network, monitor, analyze, and report on network events for anomalies and possibly malicious activity. Another way is carrying analysis within a security camera to analyze certain situations (unknown people, objects, etc.). Data privacy and security concerns associated with edge devices can remain intact with the use of data locally on the device.
- Access Control
Physically secure all networking equipment so that the devices remain out of reach of unauthorized personnel. Physical root login should be disabled and networking devices should only be accessible via a secure console. Ensure all default passwords are updated during the installation process. In edge computing, the demands of robust security functions at edge devices is high. By restricting access, the risk of intentional or accidental manipulation of resources and data can be avoided.
Edge Security and IoT
Given the essential role of edge device deployment in the IoT network, they will remain a target for attackers. The fundamentals mentioned above are key to organizations ensuring their edge devices are safe and essential to reduce system and data compromise. To reap the complete benefits of edge computing, we must realize the security needs of edge devices.
Read our success stories to know how VOLANSYS helps their client enable edge computing with security.

About the Author: Ankita Hariyani
Ankita is associated with VOLANSYS Technologies as a Senior Marketing Executive. She has the technical precision, business experience and creativity to craft technically detailed write-ups with ease. She has more than 4 years of experience in Marketing.









